

How to Install the New Tor Browser in Kali Linux
This video covers installing the Tor Browser Bundle v3.6+ (older versions work too, there is just an extra step with the new version,) on...
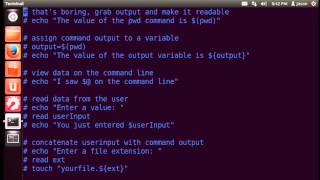

Bash Scripting Basics Part 1
Bash is a Unix shell and command language written by Brian Fox for the GNU Project as a free software replacement for the Bourne shell....
Setting up RKhunter on a Linux box and setup a Cron Job for rootkits
This on is quite easy, I use it all the time at work. How to install rkhunter! Login to your server (via SSH and su to root) cd...

Scheduling Tasks with Cron Jobs
Cron Jobs are used for scheduling tasks to run on the server. They're most commonly used for automating system maintenance or...


Why Every Hacker Should Know & Use Linux
In many of my tutorials, I have emphasized that a real hacker must know and use Linux, but I thought it might be time to emphasize and...
Exploiting a Remote System using a Rootkit
Tools Used: Backtrack R5 Windows XP Home SP1 (Due to lack of exploit updates on my system for win 7) Beast v2.07 Trojan Horse ...

Going Ghost by IP Spoofing in Kali Linux with torsocks
torsocks allows you to use most applications in a safe way with TOR. It ensures that DNS requests are handled safely and explicitly...

Changing File Permissions on a Computer
Alright, So I have taught you how to remote hack a computer, network, firewall, websites, etc.. All that good stuff! Once entering a...
Professional Penetration Testing: Hack Web Servers from Database to SSH
Proactively Identify and Address All OWASP Top 10 Threats The Core Impact Web Application Rapid Penetration Test (RPT) automates and...
HOW TO: Hacking Wireless Networks
In this video I show you how to hack a wireless network that's encrypted with a WEP key. We will be using Windows 7 and Linux. This...

