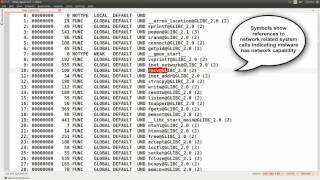

Analysis of Linux malware Tsunami using Limon Sandbox
The video demonstrates the static, dynamic and memory analysis of Linux malware Tsunami using Limon Sandbox. Limon download Link:...

How To Remotely Shutdown Any Computer
This demonstration shows how to initiate a shutdown remotely on another computer, using vector matrix technology. Easily, one can...

20 Different Types of DDoS Attacks
Types of DDoS Attacks When it comes to denial of service, there are many different types of DDoS attacks. The various terms and acronyms...


How to Hack WiFi with Raspberry Pi 2
Raspberry Pi infused with the Kali Linux Raspberry Image creates the ultimate portable hacking toolkit. You still need a Kali Linux...


Pentesting Tips - Scanning your network for Reflective Amplification DDoS
http://pen-testing.sans.org/blog/pen-... https://www.us-cert.gov/ncas/alerts/T... nmap -sU -p 53 -sV -P0 --script=dns-recursion TARGET...
HOW TO: Hacking Wireless Networks
In this video I show you how to hack a wireless network that's encrypted with a WEP key. We will be using Windows 7 and Linux. This...

How to Hack a Home Router
In this tutorial "How to Randomly Hack a Home Routers", we are going to show you how to use port scanner to identify home routers (and...
Using John the Ripper
The Hacker Academy provides a unique learning experience, teaching infosec from the hacker’s perspective. Password cracking is one of the...
Hacking with Armitage into a Network
The man-in-the-middle attack (often abbreviated MITM, MitM, MIM, MiM, MITMA) incryptography and computer security is a form of active...

