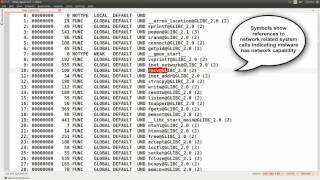

Analysis of Linux malware Tsunami using Limon Sandbox
The video demonstrates the static, dynamic and memory analysis of Linux malware Tsunami using Limon Sandbox. Limon download Link:...


How to Install the New Tor Browser in Kali Linux
This video covers installing the Tor Browser Bundle v3.6+ (older versions work too, there is just an extra step with the new version,) on...
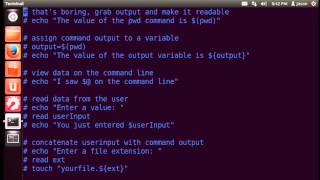

Bash Scripting Basics Part 1
Bash is a Unix shell and command language written by Brian Fox for the GNU Project as a free software replacement for the Bourne shell....


Hacking Course: Go from Beginner to Expert Hacker
Everything you need to get started as a hacker and take your hacking skills to an expert level is included in this free screen capture HD...


10 Best Android Hacking Apps
In this post we write about download best android hacking apps for your android smart phones. Now days you see pc and mobile distance is...
Setting up RKhunter on a Linux box and setup a Cron Job for rootkits
This on is quite easy, I use it all the time at work. How to install rkhunter! Login to your server (via SSH and su to root) cd...

Scheduling Tasks with Cron Jobs
Cron Jobs are used for scheduling tasks to run on the server. They're most commonly used for automating system maintenance or...

Creating a Backdoor Using Meterpreter
So, Let’s Start; You can either start the Metasploit framework from the Applications menu or from the command line. To launch Metasploit...

Simple Python Fully Undetectable (FUD) Reverse Shell Backdoor
During Internal penetration testing, sometimes you get an environment, where Antiviruses are up to date, which means that, you cannot use...


Why Every Hacker Should Know & Use Linux
In many of my tutorials, I have emphasized that a real hacker must know and use Linux, but I thought it might be time to emphasize and...

