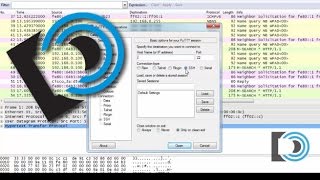

Wireshark Packet Sniffing Usernames, Passwords, and Web Pages
Subscribe! http://danscourses.com - In this beginner tutorial, I demonstrate capturing packets with Wireshark. Protocols that are...

Hacking Postgresql Database using Metasploit
Hello guys! I have been working on PostgreSQLdatabase and attempting to attack it since a few days. The reason for this is, I want to get...


Data Breaches: Top Major Companies Who Have Been Hacked
You're not just imagining it: Lately, a new data breach has been reported almost every week. Here's how to find out if your information...

Advanced SQL Injection
Sql Injection – Hacking Website In this post we will hack a website and obtain its data using SQL injection attack. We will not use any...
Professional Penetration Testing: Hack Web Servers from Database to SSH
Proactively Identify and Address All OWASP Top 10 Threats The Core Impact Web Application Rapid Penetration Test (RPT) automates and...
Social Engineering: Web Attacks
Credential Harvester Attack Method In this article, we will be looking at web based attacked using Kali Linux. Go the SE Toolkit in Kali,...

Encrypting MySQL's DB
AES Encryption Sometimes clients want that the information they collected from the user should be encrypted and stored in database. Data...
Building w/Python! Part 1: Database
The Python standard for database interfaces is the Python DB-API. Most Python database interfaces adhere to this standard. You can choose...


Google Database Hacks
Google dork Description: intitle:"Lost Password Reset" | inurl:/secure/pwreset.php | inurl:/portal/index.php Google search: intitle:"Lost...

